Tag Archives: infosec
How the right CMDB can improve your security posture

In a couple of earlier blog posts, I wrote an article about what characteristics would make a CMDB suitable for a “modern” DevOps-like environment. The first article talked about what characteristics one would like in such a CMDB. The second article evaluated the Assimilation Suite in terms of those characteristics. This article discusses how a CMDB can improve your security posture.
In today’s blog post, I’d like to do something similar – but looking at a CMDB from a security perspective. That is, this blog post is the first part of a discussion of what a security-oriented CMDB ought to look like and how it can improve your security posture.
Assimilation Versus Orchestration Tools Like Chef or Puppet?
Assimilation 2016 Security Roadmap

About a year ago, we created a security roadmap for the Assimilation Project. It’s time to update it and see how we’ve progressed since then – hence our Assimilation 2016 Security Roadmap. The Assimilation Security software concentrates on low-noise automated security tools. We expect to enhance our capabilities in best practice analyses, checksum integrity analyses, patch […]
The Unknown Unknowns

Recently, Security Week featured a great article by Emily Ratliff about “Unknown Unknowns” which explains really well how it is that the things you don’t know are those most likely to bite you. This kind of advice about what you don’t know biting you is ancient and dates back thousands of years before computers were invented.
A Half-Day To Better Security
In previous articles we gave some introductory material on how to get started with the Assimilation software for security. In this article, we go into more depth and suggest a good way to improve your security by spending a half-day with the Assimilation software. We cover setting up email alerts for security changes, fixing your security issues, and setting up the Assimilation software on more systems.
Fifteen Minutes To Better Security

Securing your systems is a daunting task – it feels like eating an elephant. When compared to hardening guidelines like the DISA/NIST STIGs, a single out-of-the-box system can have a hundred or more issues. When you multiply that by a large number of systems, despair and paralysis can easily set in. This article (fifteen minutes to better security) is first in a series which outline a process for efficiently measuring, triaging, and managing your journey towards a better security posture for your servers.
No matter your threat model, you need to understand what you have (“know yourself”). We help you begin this journey with activities which will teach you a surprising amount about your current status and the work ahead of you in 15 minutes. This article is not designed to teach you about security – I assume you know why you want to secure your servers, and have general background on system hardening.
System Management Survey
If you manage, secure, or plan for IT environments or DevOps, we’d love for you to take our System Management survey. Right now, we’re busy planning on how to make the Assimilation Suite better in 2016. Your responses will be a huge help in giving us a sharp focus on how best to improve IT management for you and others in the IT community. If you can help us out, we’ll send you a small token of our appreciation
What Aren’t You Monitoring?
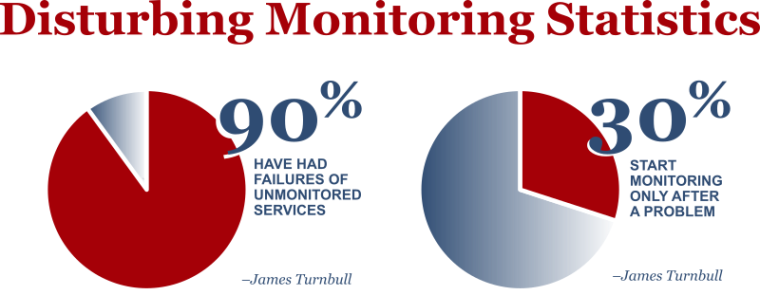
The three pillars of IT security are confidentiality, integrity, and availability. Most of the press coverage is all about confidentiality – at least until we have an airline or two or three have trouble with availability ;-). Of course, availability is also a key dimension of server management with significant operational dimensions. Those of you who know me, know I have a deep expertise in availability. Unsurprisingly, in this post, I’m going to concentrate on availability – and the necessity of monitoring everything, and knowing that you’re monitoring everything.
Ohio LinuxFest Assimilation Presentations

Last weekend, I had the honor of giving the opening keynote on Friday at the 2015 Ohio LinuxFest and a session presentation on the Assimilation project the next day. Both talks were very well-received, but the reception the Assimilation project talk received from the standing-room audience was extraordinary. So it seems good to give a summary of the talk and why I think they resonated so strongly to it.

