Lose Servers? Not Hard at all!
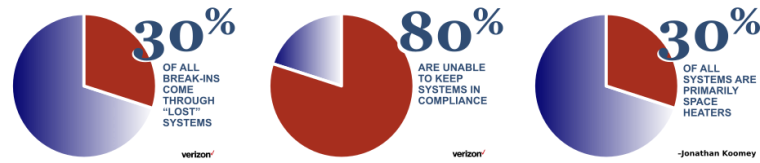
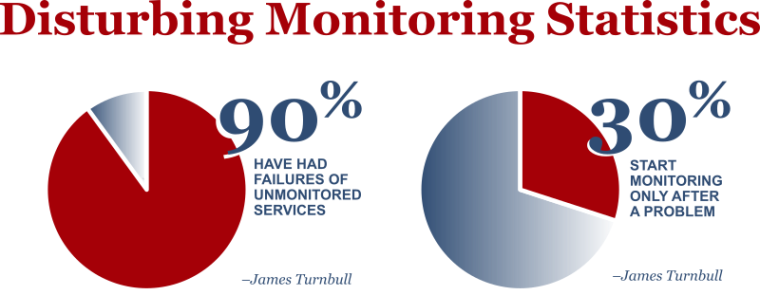
Keeping track of servers in a large organization is a daunting task, and one which many organizations don’t do well – sometimes with grave consequences. There are lots of reasons why systems get “lost”. If you can keep track of your servers, you can decrease your chances of an intruder getting in by 30%. In this article, we’ll look at what happens when you lose servers, and some of the ways people lose servers.