
Today’s blog post is about the imperative, absolute necessity for automation in cybersecurity. Those of you who read this blog regularly will note that this has been the theme for a while – with three recent articles about automation [1, 2, 3] and one on the IT best practices project (which is all about automation). In this article we talk about why to automate cybersecurity, what to automate and how to automate cybersecurity.
A good bit of the content of this post has been shamelessly appropriated from some a talk by the most excellent Ben Tomhave. Ben presented this talk at both the 2015 RSA conference and the 2015 Rocky Mountain Internet Security Conference.
Why to automate cybersecurity?
Dan Geer expertly makes the case for for automation in an excellent article in this way: “One can only conclude that replacing some part of the human cybersecurity worker’s job description with automation is necessary. If the threat space is expanding by X to the Y, then the defense has to arm up accordingly. An accelerating share of the total cybersecurity responsibility will have to be automated, will have to be turned over to machines.” Of course, the well-documented and increasing shortage of qualified security staff only increases the urgency.
An accelerating share of the total cybersecurity responsibility will have to be automated, will have to be turned over to machines.
The 2015 Verizon Data Breach Investigation Report states “It may not be obvious at first glance, but the common denominator across the top four patterns—accounting for nearly 90% of all incidents—is people. Whether it’s goofing up, getting infected, behaving badly, or losing stuff, most incidents fall in the PEBKAC and ID-10T über-patterns.”
… most [security] incidents fall in the PEBKAC and ID-10T über-patterns
It goes without saying that most people don’t intend to create a security breach through their actions. Either they didn’t know about the rule they violated, or they didn’t realize what they were doing was dangerous in this particular case. This general statement is borne out by my conversations with incident response teams. The general take from every team I’ve met with is “You wouldn’t believe what they do”. Sad, but true…
What to automate in cybersecurity?
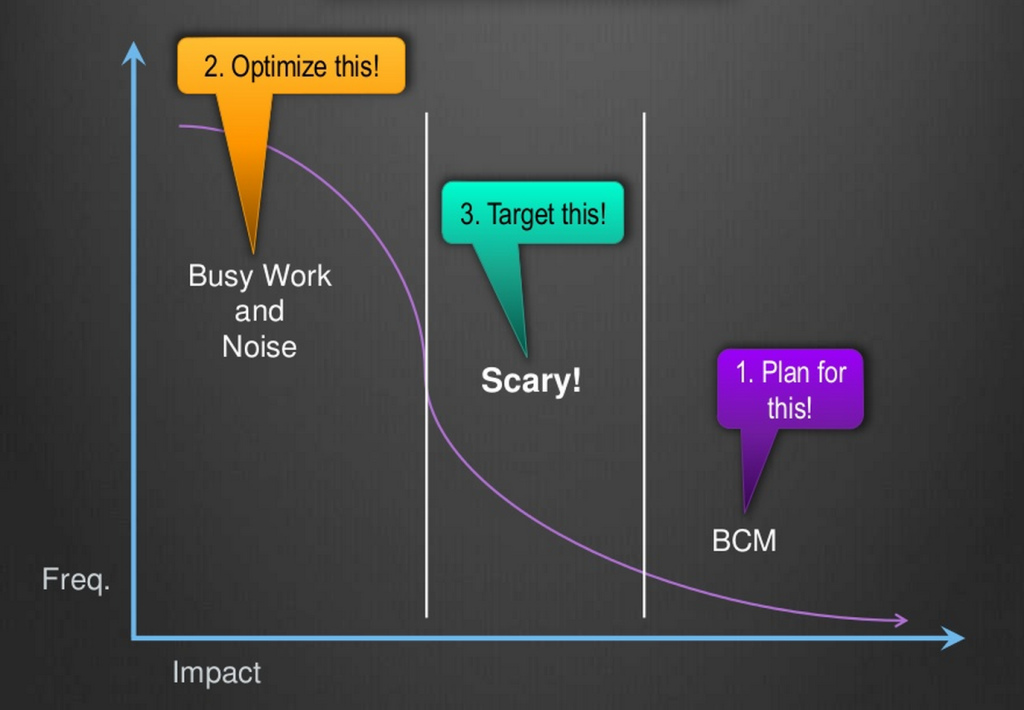
Given that the threat surface is expanding exponentially, but the number of security experts is not, the need for automation is perfectly clear. The next question that comes to mind is “What should I automate?”. In his talk, Ben Tomhave illustrates his answer to that question as a graph.
It illustates the fortunate truth that the greater the impact of a security event the less frequently it occurs. It also represents the fact that it’s easy to spend all your time dealing with the noise and busy work in security (like much of life). His general approach is sound – you have to optimize the “busy work and noise” – those things that happen all the time, and have minimal impact – so that you have enough time and resources to deal with the “scary” events and plan for the Business Continuity Management (BCM).
How to automate cybersecurity?
For most parts of the low impact work – this means automation and simplification. Unsurprisingly, I completely agree with his approach. When you approach this low-impact work, it’s important that whatever you do it not add to the noise, and not require a lot of human tuning. One of my axioms from my years in system and service availability is “Any system which relies on human reliability is inherently unreliable”.
Any system which relies on human reliability is inherently unreliable.
Of course this has to be balanced against the need to automate exactly and only that which can be reliably automated, and to ensure that we have checks and balances against errors in automation. This tension between having unreliable humans oversee an automated process in exactly the right way is covered in much more detail in Daniel Geer’s article.
At this point, I’ll put in the obligatory plug for my company – everything we do in the Assimilation System Management Suite (security, monitoring and network management) is about automating everything that can be reliably automated with as little human intervention as possible. Detailed automated discovery makes this possible. In the area of security, we’ve recently outlined our dedication to reliable security automation in our recent roadmap post.

Please note: I reserve the right to delete comments that are offensive or off-topic.